Overview
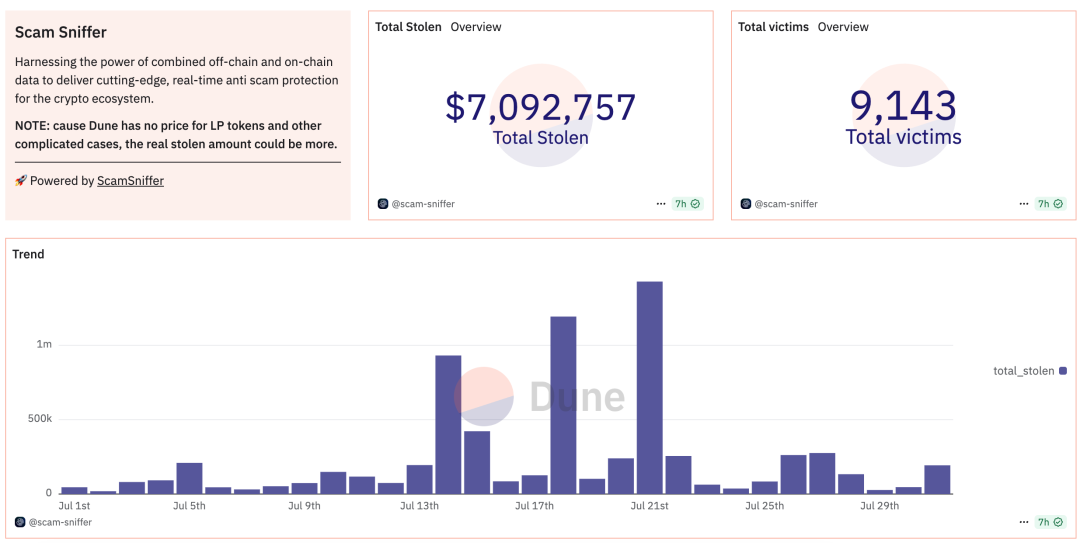
In July 2025, the total loss from Web3 security incidents was approximately $147 million. According to the SlowMist Blockchain Hacked Archive (https://hacked.slowmist.io), there were 13 hacking incidents, resulting in losses of about $140 million, with $42.48 million frozen or returned. The causes involved contract vulnerabilities, supply chain attacks, and account breaches. Additionally, according to the Web3 anti-fraud platform Scam Sniffer, there were 9,143 phishing victims this month, with losses reaching $7.09 million.
(https://dune.com/scam-sniffer/july-2025-scam-sniffer-scam-report)
Major Security Events
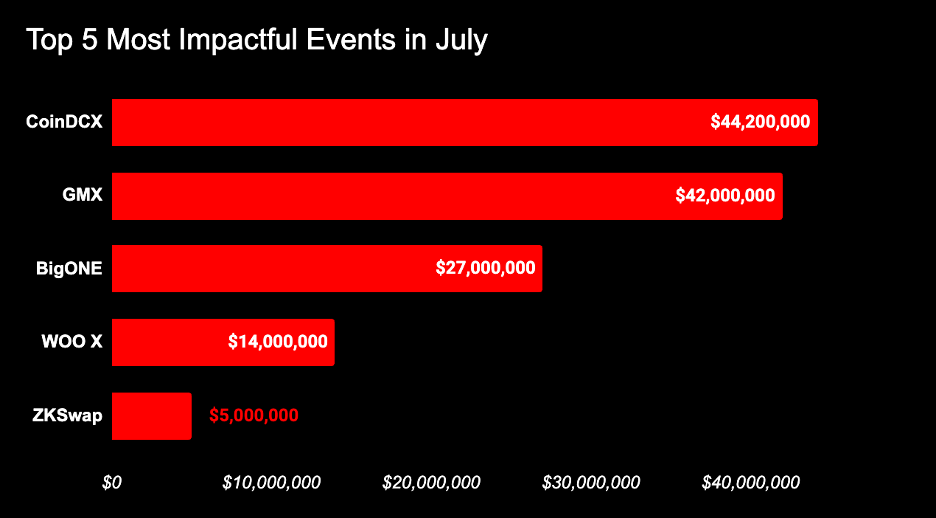
CoinDCX
On July 19, 2025, on-chain detective ZachXBT posted on his personal channel: "It appears that the centralized exchange platform CoinDCX in India was possibly stolen from about 17 hours ago, with a loss of approximately $44.2 million, but has not yet disclosed this incident to the community."
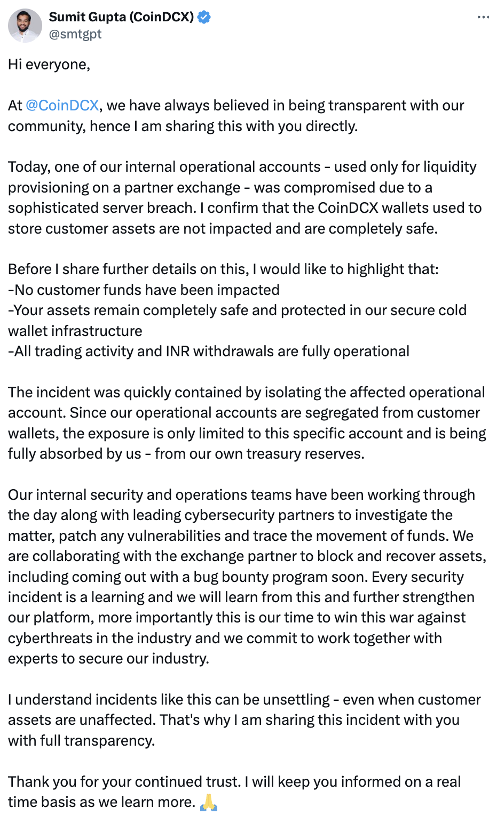
Shortly after, the company's co-founder Sumit Gupta responded on X. In his response, Sumit revealed that the attacked wallet was an internal operations account used only for providing liquidity. Customer funds were not affected as they were stored in secure cold wallets. Transactions and withdrawals will return to normal, and all losses from the attack will be covered by CoinDCX's reserves.
(https://x.com/smtgpt/status/1946597988660645900)
On July 31, according to FinanceFeeds, a software engineer at CoinDCX was arrested for assisting in the attack. The attackers installed malware on the engineer's computer under the guise of part-time work and paid a high part-time salary. The malware was a complex keylogger through which the attackers obtained login credentials and accessed CoinDCX's internal systems, ultimately leading to this incident.
GMX
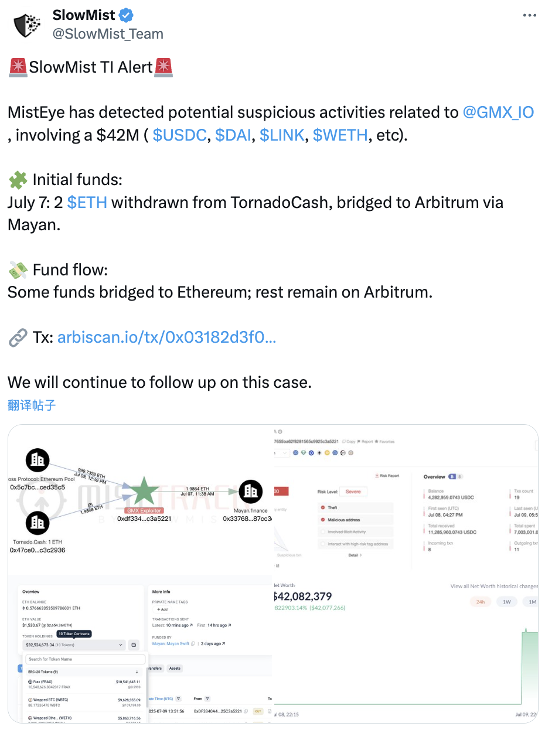
On July 9, 2025, according to the SlowMist MistEye security monitoring system, the decentralized trading platform GMX was attacked, losing assets worth over $42 million. According to the SlowMist security team's analysis, the core of the attack was that the attacker exploited the characteristics of the Keeper system executing orders with leverage and updating the global average price when shorting, but not updating when closing short positions. By using a re-entry attack to create a large short position, they manipulated the global short average price and global short position size, thereby directly amplifying the GLP price to redeem profits. For detailed analysis, see GMX Hack Analysis: $42 Million Instantly Evaporated.
(https://x.com/SlowMist_Team/status/1942949653231841352)
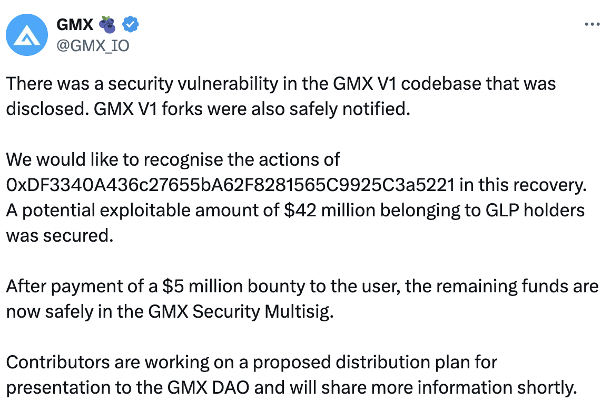
On July 11, GMX released a statement on X, saying that the security incident originated from a vulnerability in the GMX V1 code library, which has been disclosed and notified to the GMX V1 branch. To thank the white hat hacker for their efforts, GMX has paid a $5 million bounty, and the $42 million in funds involved in the attack have been secured.
(https://x.com/GMX_IO/status/1943654914749534380)
BigONE
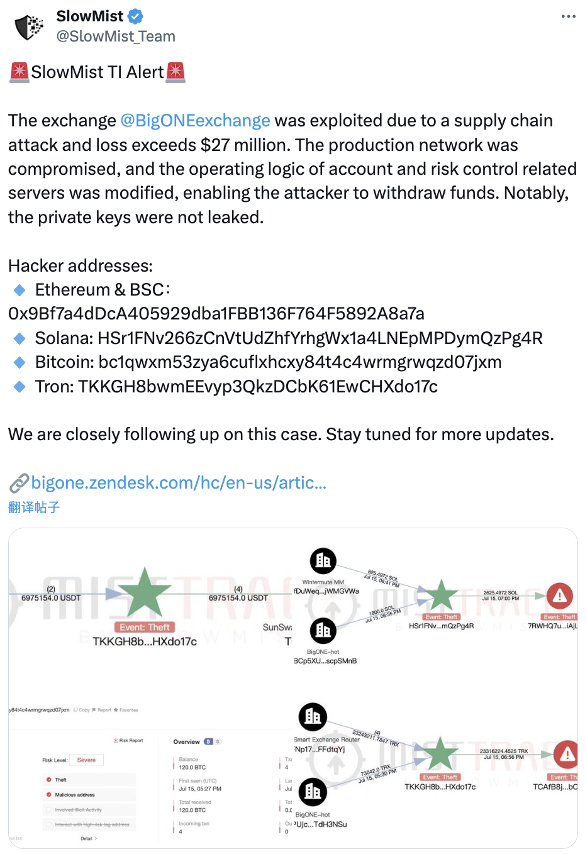
On July 16, 2025, according to the SlowMist security team, the cryptocurrency exchange platform BigONE was subjected to a supply chain attack, losing over $27 million. The attackers infiltrated their production network and modified the operational logic of account and risk control servers to enable fund transfers. On July 24, BigONE updated the event progress on X, stating that no private key leakage occurred and all losses will be covered by the official platform.
(https://x.com/SlowMist_Team/status/1945346830222680330)
WOO X
On July 24, 2025, the cryptocurrency exchange platform WOO X suspended withdrawals due to a security vulnerability, with 9 user accounts experiencing unauthorized withdrawals of approximately $14 million. According to the official disclosure, the vulnerability stemmed from a targeted phishing attack on team members, allowing attackers limited access to the trading platform's development environment, bypassing some security measures and coordinating unauthorized withdrawals from these 9 accounts.
(https://support.woox.io/hc/en-us/articles/49178783818777-Temporary-withdrawal-suspension-July-24-2025)
ZKSwap
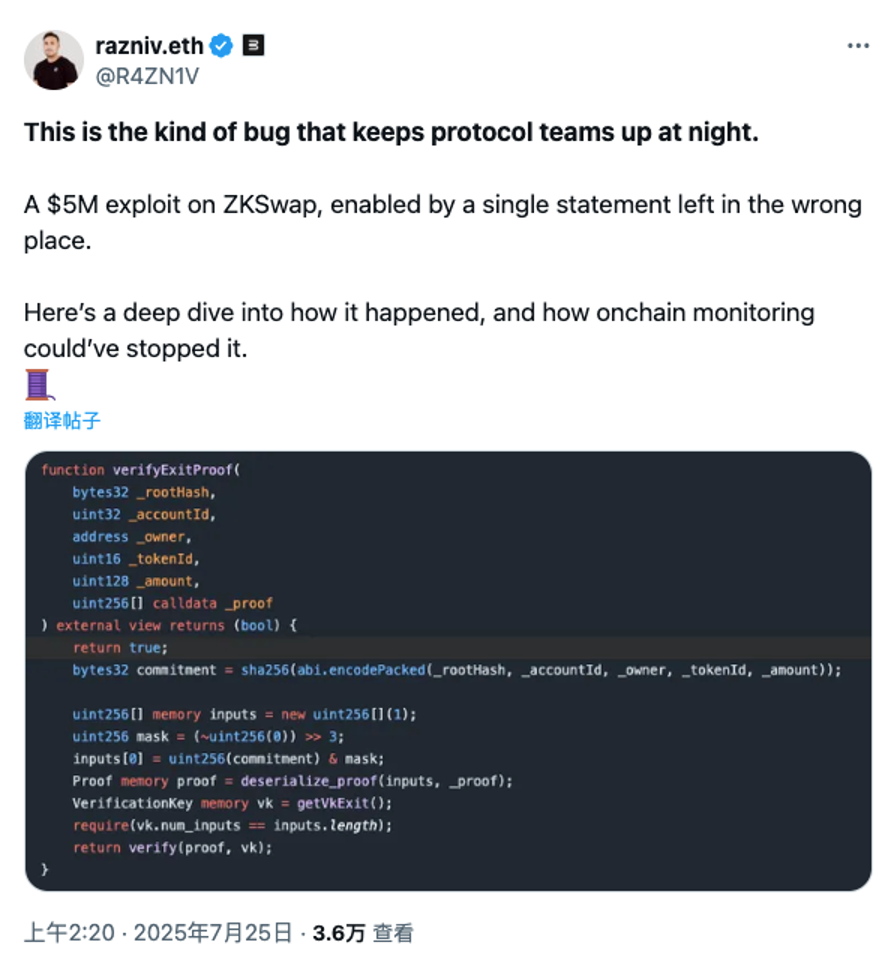
On July 9, ZKSwap's Ethereum Layer 1 cross-chain bridge was attacked, with the attacker using its emergency extraction mechanism to cause a loss of about $5 million. According to the analysis, the mechanism responsible for verifying zero-knowledge proofs was not actually performing verification. This serious oversight allowed the attacker to forge withdrawal proofs arbitrarily, bypassing the core security guarantee of the cross-chain bridge.
(https://x.com/R4ZN1V/status/1948448167734673838)
Characteristic Analysis and Security Recommendations
In the blockchain security incidents of July, contract vulnerabilities remained the primary attack method, with targets concentrated on centralized exchanges and decentralized finance platforms. Centralized exchange-related security incidents caused total losses of $85.2 million, accounting for 60.8% of this month's hacking incident losses. The SlowMist security team reminds developers that when DeFi protocols integrate complex features like leverage mechanisms and oracles, they should pay special attention to global state consistency and complete boundary condition verification to avoid systemic risks caused by interaction logic deviations. Centralized exchanges should further improve audit standards and system transparency to strengthen overall security defenses.
Besides on-chain attacks, security risks in daily usage scenarios should not be overlooked:
This month, another incident occurred where assets were stolen by purchasing hardware wallets through unofficial channels, with victims losing 4.35 BTC. The SlowMist security team previously explained this method in the Web3 Security Beginner's Guide: Common Hardware Wallet Pitfalls, which interested readers can click to view.
Recently, fake Zoom meeting phishing incidents have also been frequent: users click malicious links to enter fake meeting rooms with normal visuals but no sound, and are guided by "technical support" to download supposed repair tools, ultimately causing asset losses. Currently, the Web3 phishing drill platform Unphishable (https://unphishable.io/) has launched a "Fake Zoom Online Meeting Phishing Simulation" stage, allowing users to enhance their security awareness and protection capabilities by completing challenges.
Twitter: https://twitter.com/BitpushNewsCN
Bitpush Telegram Group: https://t.me/BitPushCommunity
Bitpush Telegram Subscription: https://t.me/bitpush